Hosting RDP Client
Background information
The Remote Desktop Servers on hosting are running Windows Server 2016 and it is very important for the end user's PCs to be up to date with Windows Updates, and on at least Windows 8. If the latest updates are not installed, the RDP session could appear to freeze regularly (due to message dialogs appearing behind the main form) or remote desktop connections could be refused altogether.
Regarding authentication, Microsoft removed support for NTLMv1 in Remote Desktop Services 2012 because it is a significant security risk so it is important to check your network security settings (see LAN Manager Authentication NTLMv2 below)
Check your Firewall
For Skills Hosting our IP range is: 31.28.78.32/28
For DWP Hosting our IP range is: 146.101.18.32/28
All external communications are via HTTPS TCP 443 and the endpoints have a wildcard SSL certificate with URL *.pellcomp.net
We recommend excluding Pellcomp’s IP addresses or *.pellcomp.net from any deep packet inspection on your corporate Firewalls / Web Proxy network appliances.
LAN Manager Authentication NTLMv2
Starting with Windows Server 2012 clients must use NTLMv2 authentication because NTLMv1 is a significant security risk:
https://blogs.technet.microsoft.com/miriamxyra/2017/11/07/stop-using-lan-manager-and-ntlmv1/
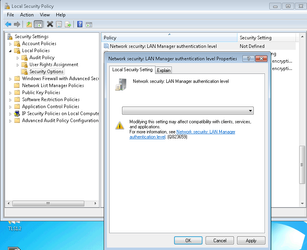
To display the version being used run secpol.msc or from a command prompt run "RSOP" and under the Computer Configuration → Windows Settings:
Security Settings → Local Policies → Security Options → Network Security: LAN Manager authentication level Properties
PICS Requires this setting to be at least as secure as: Send NTLMv2 response only (which is the default value so blank or "not defined" is also acceptable)
But the most secure and recommended setting is Send NTLMv2 response only. Refuse LM & NTLM.
Installing Windows Updates
There are a few updates which are required to connect to hosting. As they are security related it is highly likely they are already installed on your device.
All Windows versions - Update CVE-2018-0886 security update to CredSSP
https://support.microsoft.com/en-gb/help/4093492/credssp-updates-for-cve-2018-0886-march-13-2018
Remote Desktop Servers which have security update KB4103723 installed will refuse connections from client PCs which are missing the CredSSP security patch.
To determine if the client PC has the CredSSP security patch installed look for the following Windows update:
- KB4088776 (Windows 10)
- KB4088787 (Windows Server 2016)
- KB4088876 (Windows 8.1 and Windows Server 2012 R2)
- KB4088875 (Windows 7 SP1 and Windows Server 2008 R2 SP1 - no longer supported)
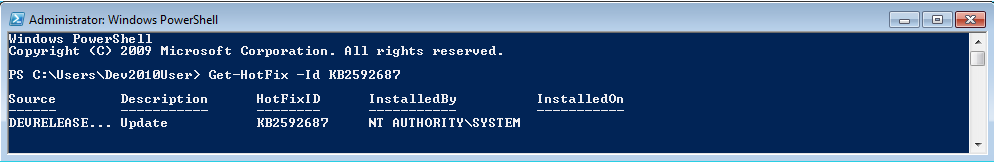
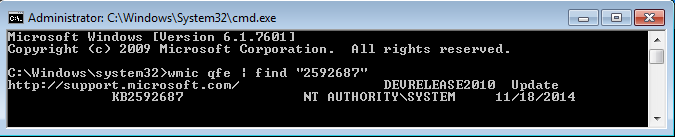
How to determine if the Updates have been installed previously
This can be done either graphically or via the command line:
Using the GUI
Control Panel > System and Security